Friday, June 4, 2010
Project 2-2: Use a Keylogger
In this practical, i have learn how a keylogger could track all your keystrokes and how the logs are read by an attacker.First, we will go to
www.softdd.com/keystrokerecorder/index.html
and scroll down and click when u see a hyperlink "Go To Download Page (Download.com)"
download the keylogger and install in on your computer.
once done, the following screenshot should be displayed on your computer.
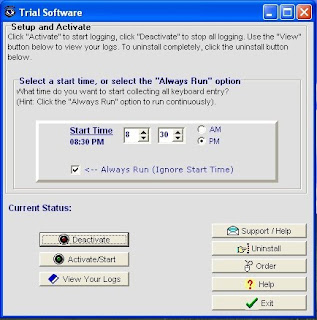
Now lets click on"Activate/Start" and click "Yes" to confirm.
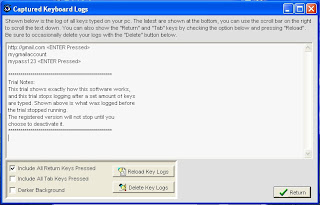
lets go to "http://www.gmail.com" and type in any username and password.
once done run the "Keyboard Collector" on your desktop and click "View Your Logs"
next, let's check where we can find the process in "Windows Task Manager"
Press "Ctrl + Alt + Del" and check whether there is a process called "keytrail.exe" under processes.
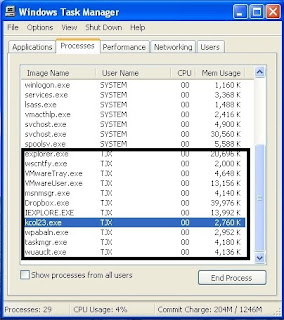
When the key logger is activated, it would be hidden from the Windows Task Manager but when the "Keyboard Collector Trail" has been opened, the process would appear in the processes.
Reflection of Project 2-2:
In this project, I learn that key loggers are able to hide from task manager processes when running and it could be easily accessible and downloaded by normal users and planted on innocent users to record their personal credentials. This would pose a high risk to users as private information are captured and sent back to the attacker.
To me, I feel that keystrokes should be encrypted to prevent key loggers from logging the keys from innocent users and capturing their personal credentials.