Saturday, June 5, 2010
Project 4-3: Hosts File Attack
In this project, i am replacing a IP address with fake IP address by editing the host fileLets open up My Computer and go to C:\windows\system32\drivers\etc
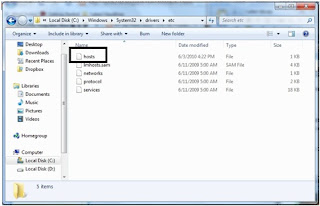
Double-Click on the file "hosts" and open in notepad
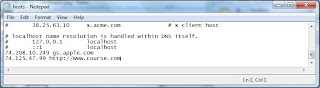
We are going to replace a website "http://www.course.com"with Google IP "74.125.47.99"
In notepad we will type in "74.125.47.99 www.course.com"
as shown in the picture below
Click on "File" and then "Save"
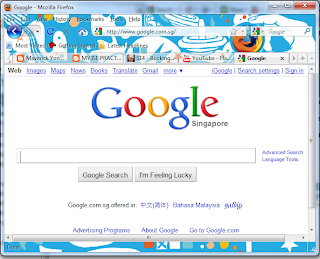
Next go to IE and type in "http//www.course.com/"
It brings me back to http://www.google.com.sg/
Reflection for Project 4-3:
In this project, i learn that hackers could hack our PC and change our hosts file and substitute a fake IP address over the real IP address and this forces us to enter the fake website. this makes it very vulnerable for innocent users and they may be lead to the fake site and think it is real site and if they typed in their own personal credentials, the credentials will be sent to the hacker.
a hacker can direct daily used sites by users to fake sites which looks to same to load viruses in their PC and could also record their usernames and passwords.
Posted by LoNeLyXx at 12:52 AM
Project 4-1: Using the Wireshark Protocol Analyzer
In this project, i am going to use wireshark to capture and decode packets to analyze its contentsFirst, lets go to http://www.wireshark.org/
Next place our mouse over wireshark and click download
Download "Windows Installer (32-bit)"
After download is done, run the program and follow the on-screen directions.
After installed go into Start, all programs and click on wireshark

Next click on Capture and then Interfaces

Next select your network adapter and press start

Next lets just go to https://www.bluehost.com/cgi-bin/uftp and type a domain "loner" & pass "123456" and press enter

It would shows Login Failed like the diagram above
Next, go back to WireShark and press Ctrl + Find and as shown in the diagram below click on String and
in the text box type in "loner" and click Find.

No text will be found as the page has been encrypted and this prevents us from finding it.
Lets test another website http://www.jobboy.com/login.php and type in "loner" in the email and "123456" in the password and press enter
Go back to WireShark and press Ctrl + F again and type in "loner" in the text box and click "Find".
It should be shown like the diagram below and in the box it shows
" .....Email=lon er&Password=1234 56"

Next click on "Capture" and click "Interfaces..." and click "STOP"
Reflection for Project 4-1:
In this project, I have learnt that packet sniffers can gain private information which may be private to a user. Hackers could use this to steal user's credentials by just using a packet sniffer. Therefore websites should encrypt their data as packet sniffers would not display the exact data and the hacker may not get the information and this would allow users to enter their private information save and secure.
Posted by LoNeLyXx at 12:51 AM
Project 3-3: Set Web Browser Security
In this project, I learnt that it is important to set browser security as it would keep my computer secure.First open up Internet Explorer and click on the "tools" and click on "Internet Options"
Make sure that it is in the general tab.
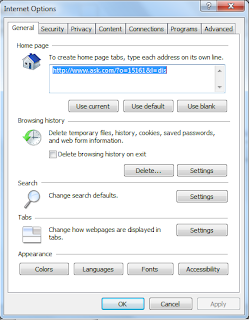
Next click on settings and click on view files
Now lets maximise the window and click on the "Last checked tab"
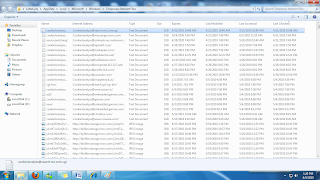
Lets open a cookie to see what is contained inside
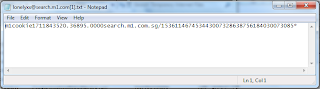
Cookies may contain user data, and this could include user's browsing habits. this could lead to hackers using this kind of information to place pop-ups that may interest the user and when the user click on the pop-up they may be brought to a site which may contain viruses, worms or malware.
Some cookies may contain more user information to make the website more user-friendly for the user.
Next, delete the files by going back to "Internet Options" and click on "Delete..." & then "delete".
Next security setting in internet explorer would be "Manage Add-Ons"
and below the "show:" dropdown box select "Run without permissions"
add-ons would make websites more user-friendly but more vulnerable to get virus attacks on the user's PC.
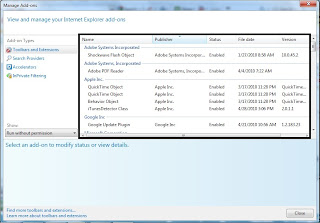
I could also change the security level higher to lessen the chances of getting infected but this would bring about inconvenience while surfing on my internet browser.
To change the security level
Go to "Internet Options" and click on the "Security" tab.
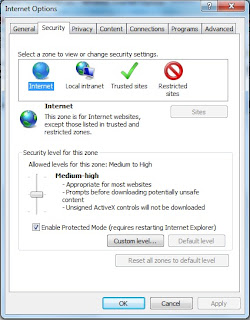
Next, click on the custom level and scroll down to Activex
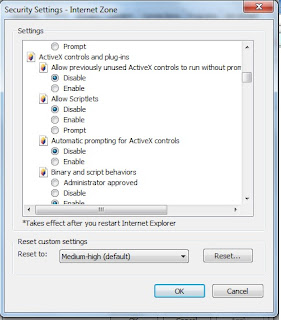
as it states, it disables unsigned Activex applications and this would set a certain level of restriction to Activex.
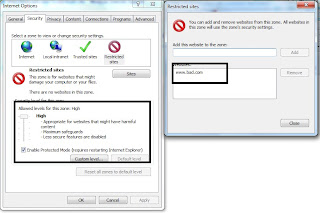
Now click on the Restricted sites and as it states the security level is set to High as this site may be infected of viruses or malicious code which may infect my PC
Next click on Sites and add "www.bad.com"
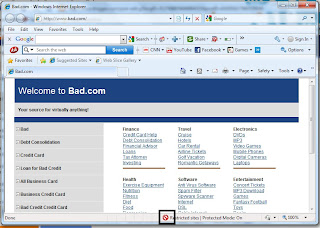
Now, in the internet explorer type in "www.bad.com" in the URL bar
at the status bar, it displays the restricted sites sign and tell me that the site is restricted to a high security
Next in the Internet Options select the "privacy" tab
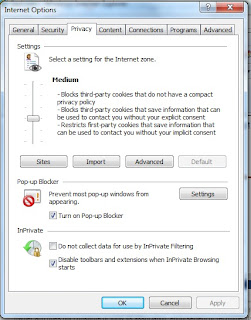
Drag the slider to see different settings from medium up to Block all Cookies
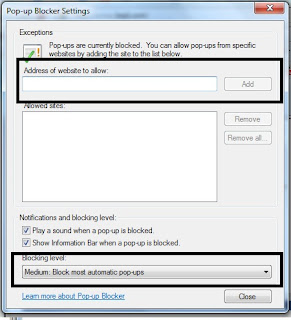
Internet Explorer also provides us with a pop-up blocker to block off irritating pop-ups.Click on tools, place mouse over pop-up blocker and click on pop-up blocker settings.
I can add sites that i want to allow them to show pop-ups and i should set the security settings to medium or medium-high
Reflection of Project 3-3:
In this project, i have learnt that although I have a antivirus installed in our PC, i should also set my Internet Browser Securities as this would provide me with a higher level of Security and this would prevent my personal computers from being hacked by hackers or malicious codes are downloaded into my PC
Posted by LoNeLyXx at 12:48 AM
Project 3-2 : Test AV Software
In this project, we are going to learn whether our antivirus have the best protection by using a fake virus.First, let's go to "Control Panel", "Security" and then click on "Security Centre"
* In Windows 7, we can go to "Control Panel" and then click on "Windows Defender"
We could also check whether our own antivirus Real-Time Protection is set to "On"
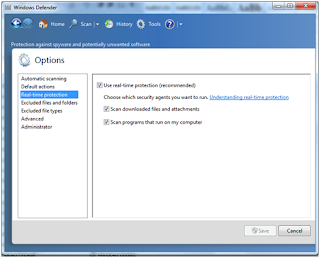
Check if the Real-time Protection is set to "On"
Next lets test using a fake virus by visiting this web page
http://www.eicar.org/anti_virus_test_file.htm
I will be downloading a file from the web page that acts like a virus.
Scroll down to the bottom and let us try downloading the "eicar.com.txt" file
When the file is clicked, my antivirus instantaniously detected it and deleted it as shown in the screenshot below
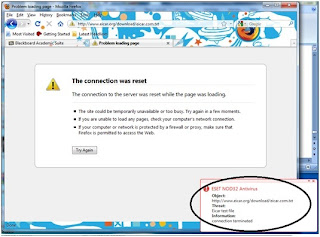
Try by downloading "eicar_com.zip" and see whether your antivirus detects it.
for mine, it got detected and quarantined right away.
If it didnt detect and let's u save it on your PC, right click on the file and click scan for viruses.
Try it for "eicarcom2.zip" and repeat the previous steps.
Reflection for Project 3-2:
In this project, I have learnt that Microsoft have their own antivirus installed in the OS to prevent viruses to a certain level even though a 3rd party antivirus software is installed. this project let us understand how strict our antiviruses are set as some may allow u to download a compressed file although it may contain a virus inside and some antivirus may quarantine right away.
I have also learnt that some antivirus has set their range on how to deal with the viruses as some files which may contain High-risk viruses are deleted instantly and some with low-risks threat are just quarantined by the antivirus.
Posted by LoNeLyXx at 12:00 AM
Friday, June 4, 2010
Project 2-3 : Block a USB Drive
In this project, i learn that i could use a program to change a USB Drive into a read only device and prevents files from being written.Firstly, we could go to
http://www.irongeek.com/i.php?page=security/thumbscrew-software-usb-write-blocker
Click on Download Thumbscrew
Next extract the downloaded file, run the thumbscrew.exe in the folder.
thumbscrew.exe should now show in the Notification area as shown in the diagram below .
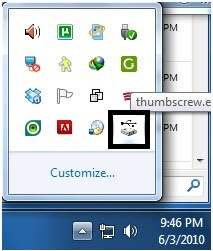
now connect a USB flash drive into your pc.
let's try to send a file into the flash drive.
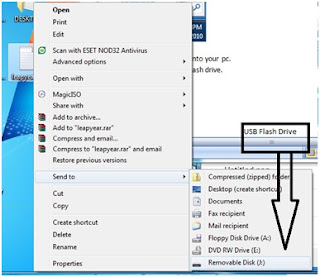
the file can be placed into the Flash drive successfully
Next, we shall right click on the thumscrew.exe diagram and click on "Make USB Read Only" as shown in the diagram below.
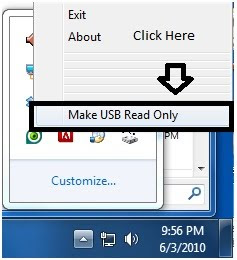
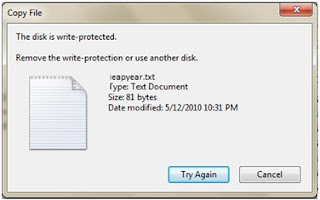
Now, we should try to send the file back into the flash drive again.
This time it should show a error like the picture below.
Reflection Of Project 2-3:
In this project, I learnt that there is a program that could block files from writing onto a Flash drive. This would prevent viruses getting loaded on Flash Drives as the flash drives have a write-protection on and this would prevent files to be written.
This shows if there are files which will be transferred to a few PCs, the flash drive should be write-protected to prevent viruses from spreading as viruses cannot write onto the flash drive.
Posted by LoNeLyXx at 11:58 PM
Project 2-2: Use a Keylogger
In this practical, i have learn how a keylogger could track all your keystrokes and how the logs are read by an attacker.First, we will go to
www.softdd.com/keystrokerecorder/index.html
and scroll down and click when u see a hyperlink "Go To Download Page (Download.com)"
download the keylogger and install in on your computer.
once done, the following screenshot should be displayed on your computer.
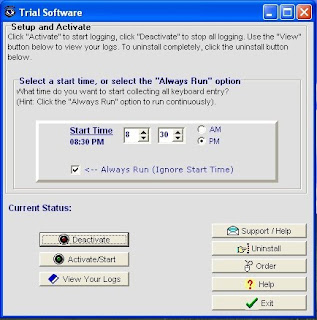
Now lets click on"Activate/Start" and click "Yes" to confirm.
lets go to "http://www.gmail.com" and type in any username and password.
once done run the "Keyboard Collector" on your desktop and click "View Your Logs"
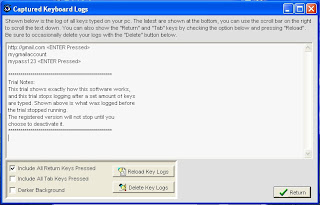
next, let's check where we can find the process in "Windows Task Manager"
Press "Ctrl + Alt + Del" and check whether there is a process called "keytrail.exe" under processes.
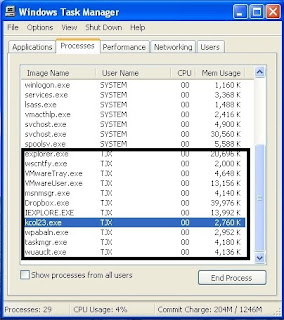
When the key logger is activated, it would be hidden from the Windows Task Manager but when the "Keyboard Collector Trail" has been opened, the process would appear in the processes.
Reflection of Project 2-2:
In this project, I learn that key loggers are able to hide from task manager processes when running and it could be easily accessible and downloaded by normal users and planted on innocent users to record their personal credentials. This would pose a high risk to users as private information are captured and sent back to the attacker.
To me, I feel that keystrokes should be encrypted to prevent key loggers from logging the keys from innocent users and capturing their personal credentials.
Posted by LoNeLyXx at 11:56 PM
Project 2-1: Scan for Rootkits Using RootkitRevealer
In this practical, we are going to use a RootkitRevealer to scan for files that may contain Rootkits.First we are going to open our IE and go to
www.microsoft.com/technet/sysinternals/Security/RootkitRevealer.mspx
next, download the file and run the RootkitRevealer.
once the program is running Click on "File" and next click on "Scan".
Let the RootkitRevealer scan through your Computer first.
Once done, at the bottom it would state "Scan Complete"
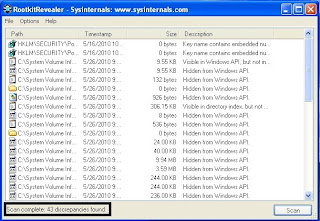
RootkitRevealer would also include discrepancies in the Registry and any of the discrepancies found may not neccessary be a Rootkit.
Reflection of Project 2-1:
In this Project, i learnt that i could find a freeware on microsoft which i could use regularly to scan my computer for rootkits. A rootkit is a software designed to gain administrator-level control over a computer system without being detected and this shows how rootkits pose a high-risk threat to users.
Posted by LoNeLyXx at 11:55 PM
Project 1-4: Scan for Malware Using the Microsoft Windows Malicious Software Removal Tool
In this Practical, we will be downloading Microsoft Windows Malicious Software Removal Tool. If your computer has Automatic updates turned On. Microsoft Update would have installed a updated version of Microsoft Windows Malicious Software Removal Tool which runs in the background.Firstly, Enter "http://www.microsoft.com/security/malwareremove/default.aspx" into your IE.
Click on "Skip the details and download the tool"
Next, Click on Download.
Save the Program to a desired location.
Click Run when the download completes and follow the default installation instructions.
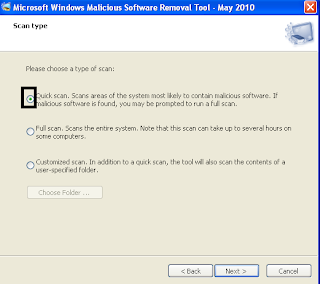
Select "Quick Scan" when asked to choose "Scan Type"
When the scan is done, determine if there is any malicious software that is found in your computer
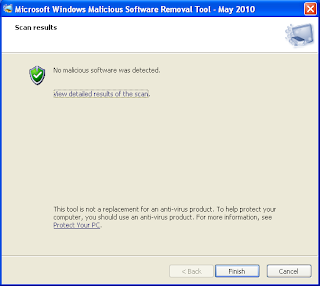
Next, Click "View detailed results of the scan"
if any malicious software is detected re-run the scan and change the "Scan Type" to "Full Scan".
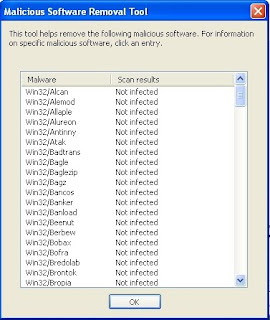
Reflection on Project 1-4
In this project, I have learnt that we could also download the microsoft malware scanner to remove any files which are infected with malware as windows also install a malware scanner running in the background may not detect the malware.
this project shows us that instead of using a antivirus to scan for a wide range of viruses which may take a long time, we could use this malware scanner to scan through our computer for any system files which are infected.
Posted by LoNeLyXx at 11:52 PM
Project 1-3: Inspect for Insecure Versions of Applications Using Secunia Software Inspector
In this practical we learn that it is important that security updates are applied in order that computer systems remain secure. Unpatched programs are becoming target to attackers. Most softwares does not have the feature like Microsoft that will automatically patch updates.One solution to this problem is to use a online software scanner that would scan through your computer to out dated programs and alert you for any unpatched programs. One of the online software scanner is the "Secunia's Software Inspector".
Firstly,
Enter the URL in your IE "http://secunia.com/vulnerability_scanning/online/"
Click on "Start Scanner" and accept any default warning.
This searches Programs in your computer and displays programs which are Out-to-date.
Check the box "Enable thorough system inspection" as shown in the example below.
This would allow the Inspector to search for programs that are not stored in their default locations.
Click on "Start"
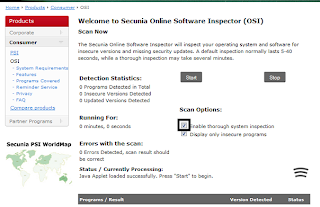
the scan is complete, it should display like what is shown on the diagram below

Reflection of Project 1-3
In this project, I learnt that other than just updating Microsoft Updates, we do need to update 3rd party programs which are also installed in our computer. the updates patches the loopholes and bugs of the programs to make it more secure and I am able to use a online program scanner to scan through all my 3rd party programs and tell me which of them are outdated and it is time to update them.
Although there is a online scanner on the web, I should also check the program on the developer websites to check for any available updates as the online scanner may not be up to date and will not detect the outdated programs.